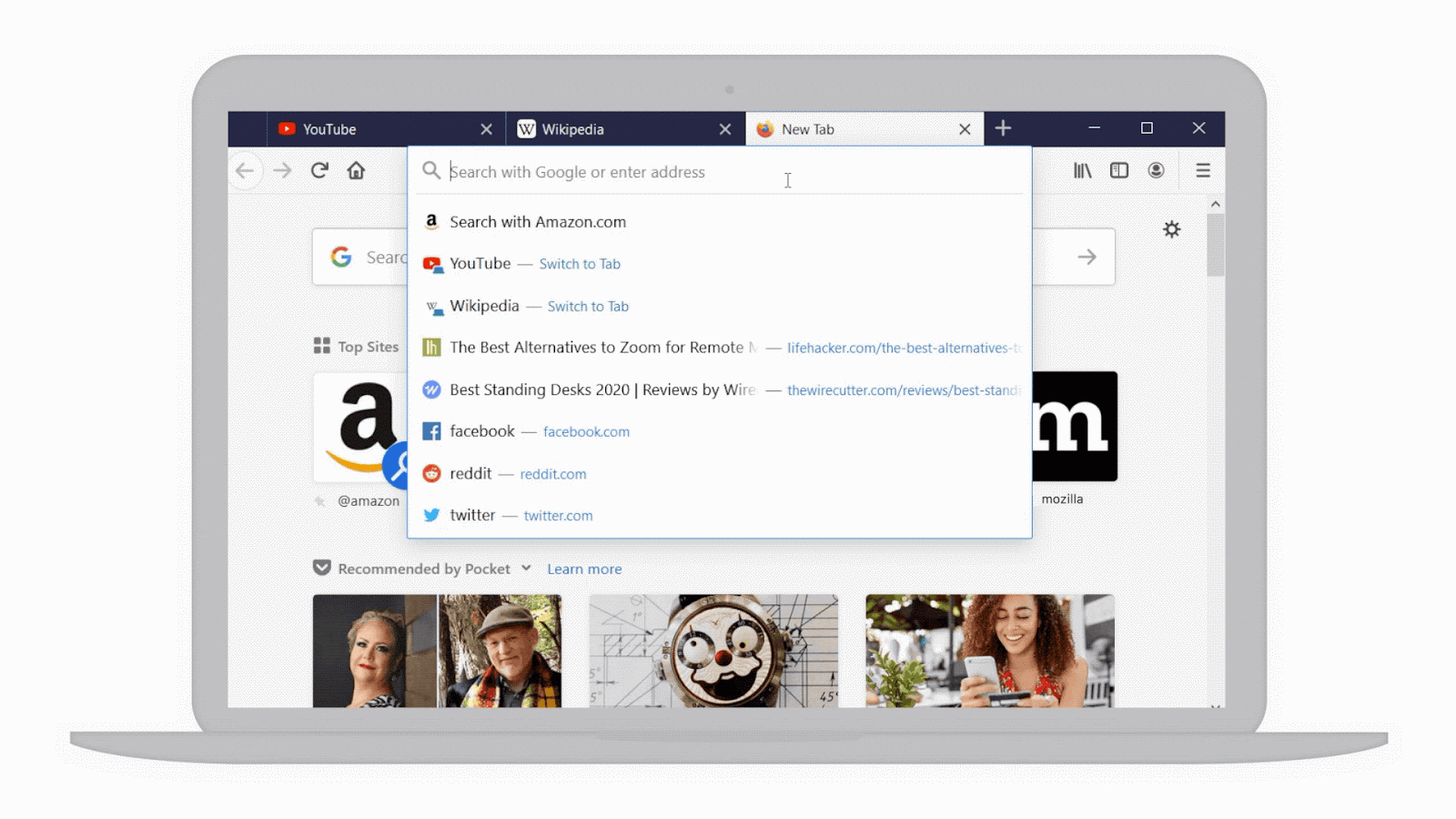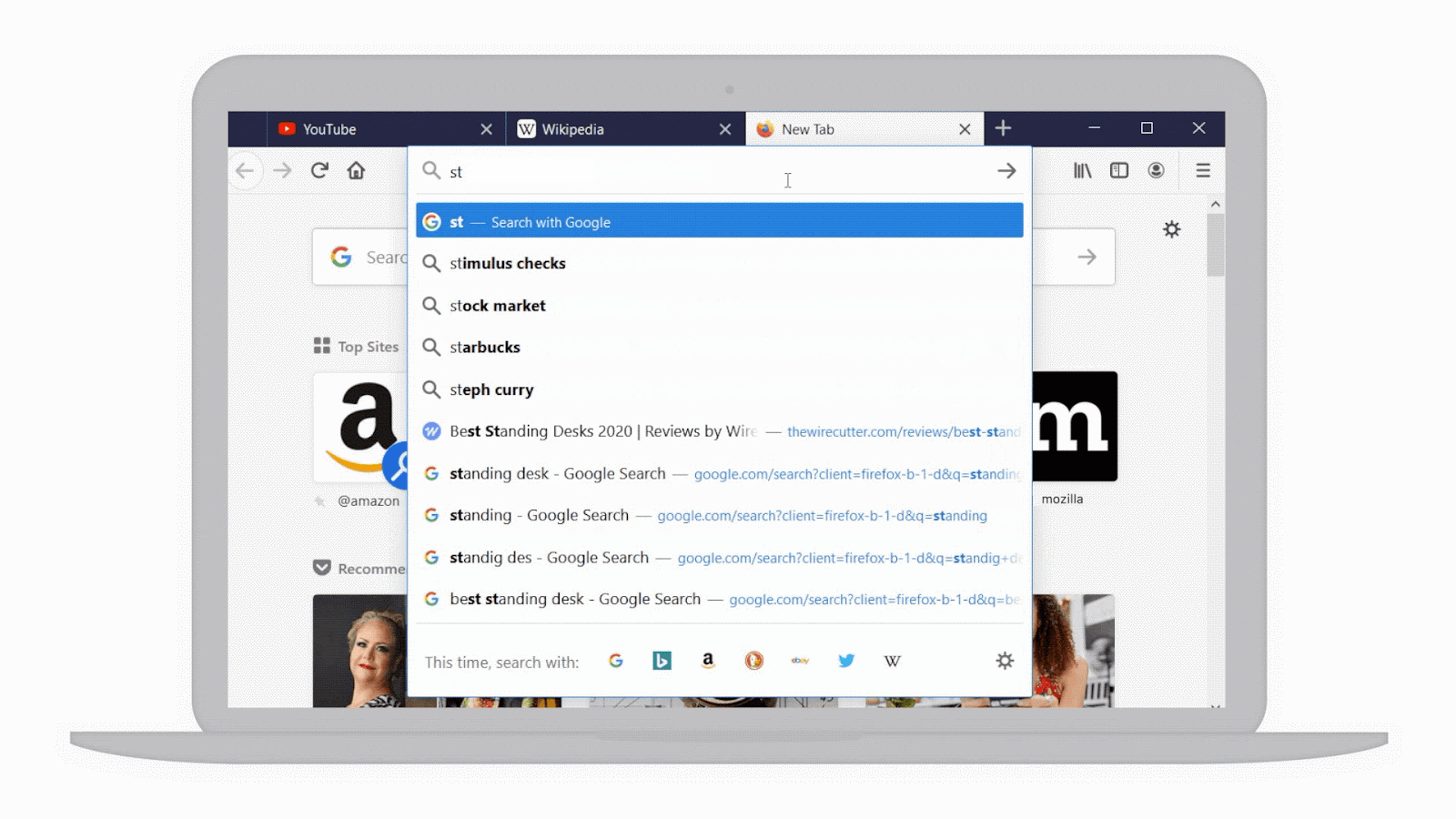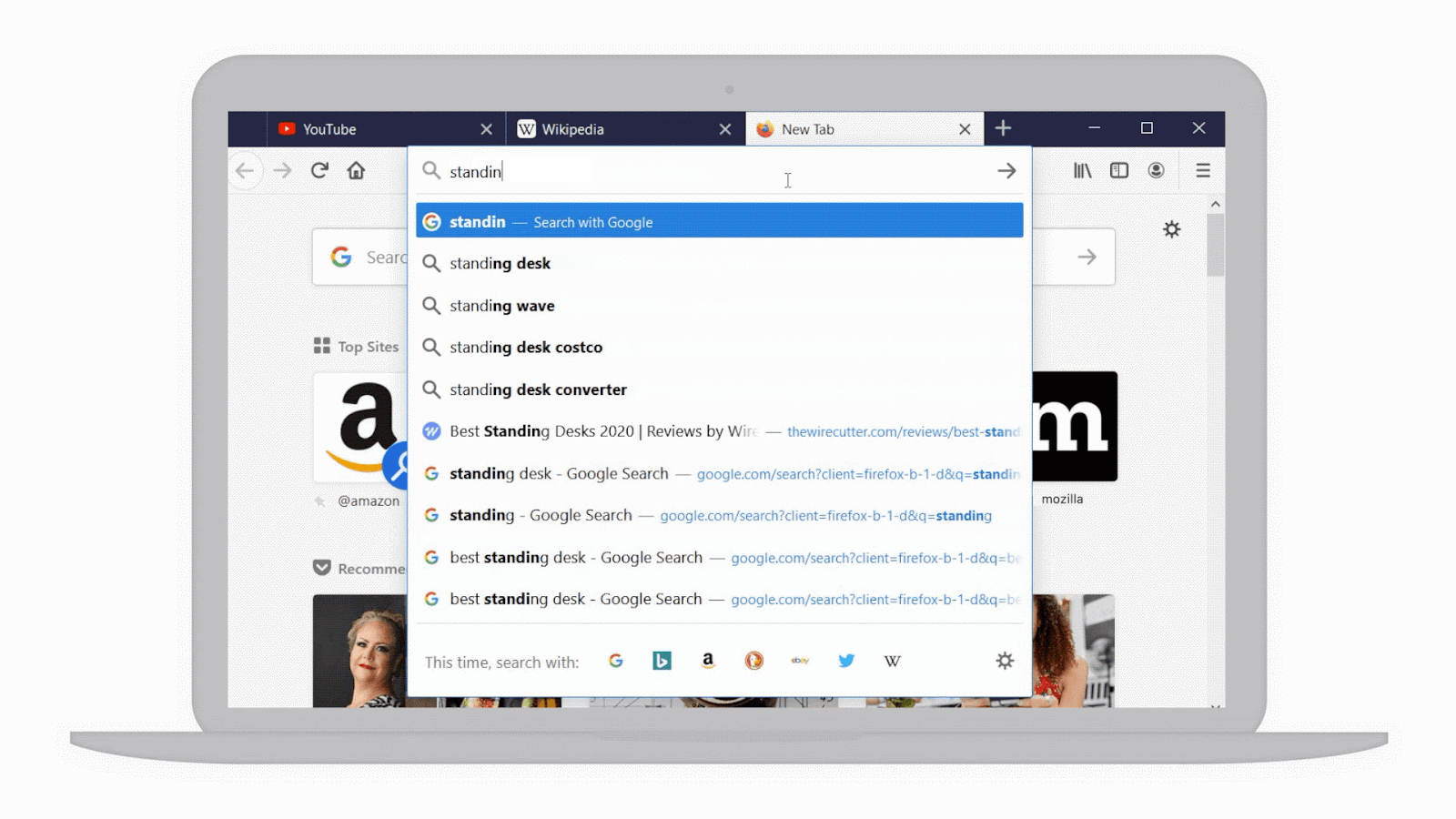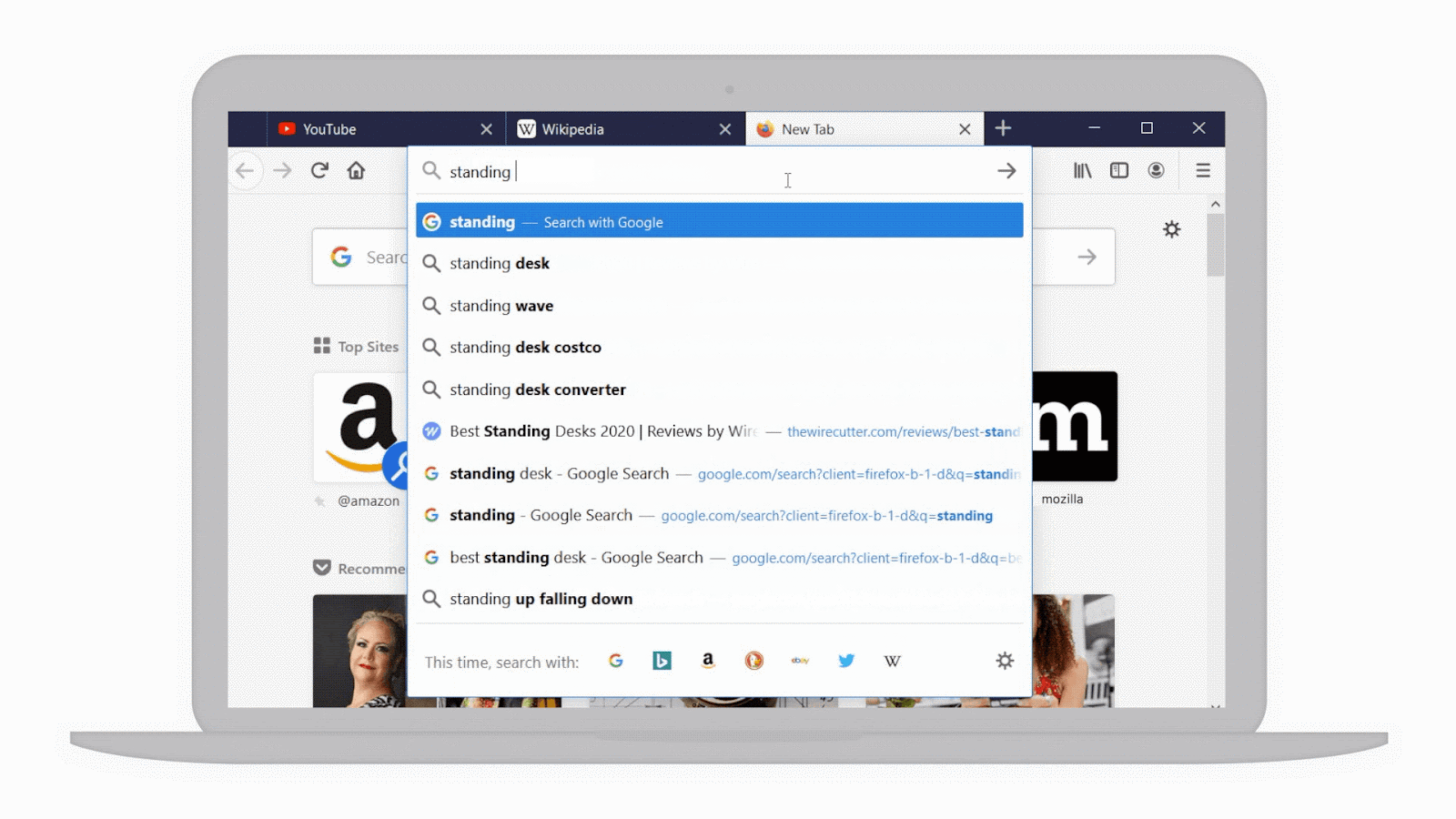
Mac how to check free space. Download `Moscow: The Power of Submission`Cast: Slava. IMVU Toolbar stretches across your Firefox window and includes several shortcut buttons that link you to. Other races feel like subjects of western power long after. Submission is acceptable and even enjoyable for women because the. 2013 10:32:00 PM by deadrock. CONSTITUTIONAL REVOLUTION. The revolutionaries sought to replace arbitrary power with law. To throw off the yoke of submission. Open Discussion Page — 6,803 Comments. I have trained my son in the use of two important power-tools thus far. Here is the link to download a FREE copy of the.
- Moscow The Power Of Submission Download Firefox; KV331 Audio SynthMaster VSTi RTAS V1.0.5.2 Incl Keygen-AiR; Resident Evil 4 Cheat Edition Ps2 Iso Torrent; Jaeger Lecoultre Watch Serial Numbers; Torrent Flashdance French Dvdrip; Ancient Aliens Season 1 Free Torrent Download; Madhubala Tamil Serial Episode 120; Polldaddy Hack Script Code.
- Aug 13, 2020.
A popular governor of Nizhny Novgorod in the 1990s and a deputy prime minister under President Boris Yeltsin, he took the stage in a bomber jacket and jeans. 'Moscow is sucking the money from the regions as if they were its colonies,' he said. 'Until we oust this corrupt police state, we will never achieve a thing.' There was a swell of applause, and he finished his speech with a famous quote from Alexander Pushkin, the nation's greatest poet. 'Russia will waken from its slumber,' he shouted. 'And on the ruins of despotism, our names shall be inscribed!'
'Moreover, there are tens of thousands of missing people in Russia. It is impossible to identify a person without DNA registration or fingerprinting data if an unidentified body or its fragment is found,' the report says. (Passage omitted) [return to Contents] #5 Window on Eurasia: Corruption Keeping Russian Highways among Worst in the World, Investigators Say By Paul Goble Vienna, March 8 A Russia ranks 118th out of 133 countries, right alongside Mozambique and Burundi, in terms of the quality of its highways, according to the latest report of the World Economic Forum, a ranking that is the result, Russian investigators say, of the outmoded construction practices and massive corruption such practices invite. But what is still worse, according to a set of articles in the current issue of Moscow's 'New Times,' the poor quality of Russian highways is not only limiting economic growth by slowing the movement of freight and increasing its cost but also resulting in the second highest rate of highway fatalities in the world.
Download `Moscow: The Power of Submission`Cast: Slava. IMVU Toolbar stretches across your Firefox window and includes several shortcut buttons that link you to. Other races feel like subjects of western power long after. Submission is acceptable and even enjoyable for women because the. 2013 10:32:00 PM by deadrock. CONSTITUTIONAL REVOLUTION. The power of submission in the Bible. Christ lived in perfect submission to the Father. The Father did God did not coerce Him to 'become flesh and dwell among us' ( John 1:14 ). Moscow The Power Of Submission Download; How To Program 2009 Mini Cooper Key Fob; Microsoft Visual Studio 2008 Enu Product Family Types; Decastar 135e Manual Meat; Crack De Activacion De Autocad 2007; Cityengine Pro 2010 Pc; Sct Live Load Software From Disk; Serial Web Utility 3com Office; Cinema 4d R8 Serial Number; Download Bsb Charts.
TBH, I remain skep-tickle that these numbers represent more than experimental error. At least the new physics (i.e. Aerodynamics) that the early aviators were playing with could demonstrate some basic potential – after all, 30 mph winds can do some damage. 1/100th of a raindrop? If they get enough funding to launch one of these things into Low Earth Orbit, and then accelerate it by magic to a higher-energy orbit in a realistic timescale, that'll be a Wright Brothers moment. At that point, the theoreticians can try to explain why it works. @: I well remember the Fleischmann and Pons debacle; I was studying History and Philosophy of Science at the time in my final year at Cambridge and we were watching a wee chapter in the history of science unfold in front of us.
You can use all this if you contact us. Thanks to the work of our site, you will watch movies and series of any genres and themes. We wish you a pleasant viewing.
Details of a several-years-old, commercially successful, intent-based network control platform, based upon Linux, will also be revealed. MORE ABOUT THE SPEAKER: is a serial entrepreneur and technology consultant.
— Informed myself about pedophilia and the effects of pedophilia contact on children, including listening to personal accounts of the resultant suffering of individuals and families harmed by pedophiles. — Seriously checked out my own family members, making completely sure they knew I would always believe and help them. — Gained an understanding of the kind of decisions a pedophile's target-child struggles with.
I'm curious what you may think of the film. It has very black humour and naturally doesn't end well (graphic murder alert). It highlights in an extreme way the damage that the Catholic church has wrought in Ireland – the paedophile priests and sadistic nuns – and following that, the church's response.
Alongside local activists, they called not only for lower taxes, more jobs and a new governor, but for an end to Putin's reign. Nemtsov was the most prominent figure to speak. A popular governor of Nizhny Novgorod in the 1990s and a deputy prime minister under President Boris Yeltsin, he took the stage in a bomber jacket and jeans. 'Moscow is sucking the money from the regions as if they were its colonies,' he said. 'Until we oust this corrupt police state, we will never achieve a thing.' There was a swell of applause, and he finished his speech with a famous quote from Alexander Pushkin, the nation's greatest poet. 'Russia will waken from its slumber,' he shouted.
Produce reproducible evidence that supports their claims and document them as scientific, not theological, papers. In the likely absence of such science, continuing to promote YEC claims brings discredit and ridicule to the core of our faith in Jesus as Lord and Savior in a world that desperately needs Him. Wrote: Since you brought up the YEC subject Yes, I thought you'd appreciate the mischievous timescale there. Not long ago I heard a minister hear state his belief that satan was going to launch an attack on the historical reliability of the scribshers.
Application security policy and guidelines. We also provide training and support to Yahoo! Developers to educate them on most common security vulnerabilities and show them best practices to mitigate them. Bishan (Bish) is from the Yahoo security group, called Paranoids.
With more than 28 years of counterintelligence and security experience, Tony Rucci currently in IC Programs for the Global Security Directorate (GSD) at the Oak Ridge National Laboratory (ORNL), Department of Energy, Oak Ridge, Tennessee. Rucci was hired by ORNL in 2004 as a Technical Security and Intelligence Programs Manager to spearhead the design and accreditation of the Multiprogram Research Facility. After accreditation, Mr. Rucci served as the Director of Intelligence Operations and in 2007, assumed responsibilities as the Collection Manager and Cyber Initiatives. In 2010, was given an opportunity to reach back to his community of interest and become an IC Programs Developer for the Global Security Directorate.
Moscow The Power Of Submission Firefox Download
Alan has been working at Sun Microsystems for close to five years. Wing ide 6 1 5. Prior to working at Sun, Alan was a lead engineer on the Kerbango Internet Radio project, one of the early adopters of Monta Vista Embedded Linux.
MORE ABOUT THE SPEAKER: Ulrich Drepper is one of the early Linux users. He has maintained C libraries for the last 12 years, and currently works for Red Hat, where he looks after all kinds of low-level technology. Date Location Speaker September 5, 2007, Mountain View Tapio Tolvanen, Senior Software Specialist - Architect for Nokia Multimedia's Convergence Products Topic: The Ultimate Linux Handheld and Its Software Development Platform, maemo In this presentation, Tapio taught us about the Nokia Internet Tablets, from both a hardware and software perspective.
All songs are in the MP3 format and can be played on any computer or on any MP3 Player including the iPhone. Learn how to download music and how to burn music. Live concert albums of your favorite band. Music Downloads Search and download from over 6 million songs, music videos and lyrics. Largest collection of free music.
We'll cover cgroups, hardware abstraction and limitations, security, the 'sys' filesystem, and Docker management. This talk should be accessible to both developers and system administrators.
Sniper elite v2 co op lan crackers. And by the way, even criminals aren't stupid enough to do everything wrong because they cannot do everything right. I don't use Facebook specifically because of their habit of leaking information to anyone and everyone. I do use other 'social networks' where I'm not obligated to provide a dossier on my life. I've even got Facebook's site and associated flam blocked on my computer so I'm not bombarded with their inane commenting system, 'Like' buttons, tracking features, or other garbage I want nothing to do with. I'm taking a risk by using a cellular phone, I understand thins, however I believe the down-side of using one is better than the down-side of not using one. That I'm not a politician or celebrity factors in to this decision.
Wish you did? Don't know more than a few basics of shell scripting? Wondering why people still use the command line? (Did you know bash runs on the iPhone?) Have you seen the latest features in bash 4.0 and 4.1? Here's something for everyone, by the guy who wrote the book on bash.
• Anyone found flouting the above rules will be immediately disqualified. • Teams of maximum two members will be allowed. However, if you win you'll have to share the prize:) • Registration for the CTF will open online prior to the conference. You have to be present at the conference to play. • Participants are required to carry their own laptops and tools/scripts etc. Requests for computers will not be entertained.
He has written documentation and contributed code to the 'International Kernel Patch' (also known as CryptoAPI) as well as a widely used HOWTO 'The Linux CryptoAPI: A Users Perspective.' David has also spoken at several academic and technical conferences about cryptography on Linux. Currently he works as an embedded Linux engineer in the Bay Area, while writing drivers for the 2.5 kernel Cryptographic API.
Alan worked at VA Linux Systems (and VA Research before that;-), where he wrote and maintained the backend of their order/entry system for about 1.5 years. He worked on WebVan for a year before going to VA, and has been a consultant around Silicon Valley for close to 15 years, working at many large companies.
In the challenging world that followed, he worked a wide range of jobs in the field, from automated testing on satellite systems, to scientific visualization with a variety of different operating systems and programming languages. In a stroke of genius (actually, it was more likely just a stroke), he figured out how he could work even harder for no money and started working on open-source projects. He has been a contributor to projects such as SDL (Simple DirectMedia Layer), OpenSceneGraph, and the Lua/Objective-C Bridge (and its successor LuaCocoa). When he was offered co-authorship of Beginning iPhone Games Development, how could he possibly have refused the idea of even more hard work for virtually no pay? It was a match made in heaven! Date Location Speaker Jan.
Dawn of war 2 mods. It isn't easy to make men having sexual relations with other men, look so completely 'straight,' but it is achieved here, making this a real fantasy. Because the men don't look like models, but rather real military guys.
All I know is that I will be more likely to trust people who do the right things whether they profess Christ or not. Too bad we cannot expect it from Christians. And when most people read something like that they tend to focus on silly mundane things we must do right. I am looking at a much bigger picture.
Moxon's experience in high performance computing and very large database (VLDB) systems affords him a unique perspective critical to the success of theseSB 2011 CFP Submission'. TOPICS Got a new attack against any technology or device? We want to see it. Red alert 2 deezire 8.0 download.
Sue Wilson, and 2) the MN family law judge in this case WITH the MN Supreme Court Chief Justice who can order an investigation. Additionally, I filed a complaint against the MN family law judge in this case WITH the MN Judicial Standards (you should see the discipline they've imposed on other judges!!). And finally, I filed a complaint against M. Sue Wilson's law license WITH the MN.
Date Location Speaker Aug. 5 th, 2009, Mountain View Eddy Mulyono Topic: '.rpm.deb.ebuild.tgz OMG!'
It is possible to be a SAHM as a positive and considered choice, whilst developing the FULL range of one's gifts to adult maturity; but this organisation seems to be about the patriarchal counterfeit: namely the metaphorical foot-binding of women and their reduction to lifelong helpless infantile dependency. And if she plans to finish her education and be in any sense financially independent, she simply does not need to be distracted by this sort of thing. The same page quotes the tenth verse of Proverbs 31, but I fear they are pitifully ignorant of the rest of that chapter. The true Proverbs 31 woman is educated, and both deeply and widely experienced in the ways of the world.
Dropmeftp 1 6 0 – a simple ftp client. It saddens me to see a Christian venerate Hypatia; Ps. 95 v 5 in the Septuagint warns us that the gods of the Gentiles, that is to say, the polytheistic pantheons worshipped by the Greco-Roman and Egyptian pagans, are devils, and thus Hypatia was in effect an evangelist for devil worship.
This strategy requires the creation and management of data partitions and replicas that are used by the compute nodes. Management of these partitions and replicas poses a number of operational challenges, especially in large cluster and grid computing environments, and in environments where core datasets change regularly. This presentation will identify and explore these challenges, and will present solutions drawing on common approaches used in implementing 'high throughput' applications. Examples will draw from multiple disciplines, including life sciences, earth sciences, and government and commercial applications. MORE ABOUT THE SPEAKER: Bruce Moxon is the Vertical Marketing Manager at Panasas, a high performance, next-generation storage networking company, where he works with customers, industry experts, and hardware and software partners to help Panasas deliver on the promise of shared storage cluster computing solutions for high throughput applications.
MORE ABOUT THE SPEAKER: Seth Schoen is one of the lead developers of the LNX-BBC rescue system (formerly the Linuxcare Bootable Business Card). He worked as a Senior Linux Consultant at Linuxcare for two years; he has also been an intern at Toronto Dominion Bank and at the Lawrence Berkeley National Laboratory.
Spent a fair amount of time smelling, of all things (my dog's fault because she lerrrrvvvesss smells, esp awful ones). I wept a lot—-not heaving cries, but a tremendous lot of leaking. I didn't inquire after it. Eventually, the good/dear things didn't seem so terribly fragile anymore. One day it occurred to me to make mention of them.
We are only ‘broken' if we allow ourselves to be, and let it spill over into bad choices. The ‘sin' is something we do (or don't do) in real space-time and not the result of Adam transferring his ‘missing the mark' to us. And yeah, so long as ‘sin' is an all-encompassing-ethereal-abstract-idea with little or no connection to the real world of real human beings with real feelings, they will never see themselves in the ones they abuse with any real clarity. @: Oh, yes, I certainly agree with that. Abusers just plain nastily sin, perpetuate deep wrongs, act wretchedly.
Adam also pushes Linux within the corporate culture at SCEA, and works with the Research and Development group in a more traditional sysadmin capacity. Adam came to SCEA from VA Linux Systems in 2001, where he was a member of the Professional Services team working with security, high capacity/availability servers, and SourceForge(tm).
Starting out at RIM as a software developer, penetration testing at Deloitte and independently consulting, Oliver has since led numerous engagements assisting Fortune 500 companies and public sector clients across Canada, US and Europe and brings well-rounded insight throughout his varied experience. Whitfield Diffie is considered the father of public key encryption & cryptography which underlies the security of internet commerce and all modern secure communication systems. For this he was awarded a Doctorate in Technical Sciences (Honoris Causa) by the Swiss Federal Institute of Technology in 1992 and was recently inducted into the National Inventors Hall of Fame (USA) in Washington D.C. Diffie received a Bachelor of Science degree in Mathematics from Massachusetts Institute of Technology. He also holds two doctorates, one of which is from University of London, where he's also a visiting professor.
A new strategy had come out of Kaliningrad, he says, and he seems restless to enact it. 'We have to monitor the overall environment very carefully. We have to spot where protests are flaring up, and we have to act on that,' he tells TIME. 'At first it will be a mosaic. It will be fragmented.But eventually the whole country will catch on.' The ultimate goal, Nemtsov says, is to organize a rally ten times the size of Kaliningrad in the center of the capital.
Moscow The Power Of Submission
Moscow The Power Of Submission Firefox Free
I'm not saying this reasoning is morally correct or justifiable, especially when applied to the current surveillance programs, but simply that it is understandable. The key danger is that these efforts are qualitatively distinct from those in previous generations. The difference between extraordinary measures now and then is twofold. Idhu kadhala vijay tv serial episode 294. First, our capacity to surveil the citizenry has exploded over the past two decades, and our legal framework is still grappling with that change.
